In an age where information is a valuable asset, safeguarding sensitive data is of paramount importance for businesses, organizations, and individuals alike. With the exponential growth of digital communication and collaboration, the need for secure data sharing and storage has led to the rise of virtual data rooms (VDRs).
These platforms offer advanced security features that go beyond traditional file-sharing methods, ensuring the confidentiality, integrity, and availability of critical information. Let’s explore the enhanced security features of today’s modern virtual data rooms and their significance in maintaining data protection.
Document Control
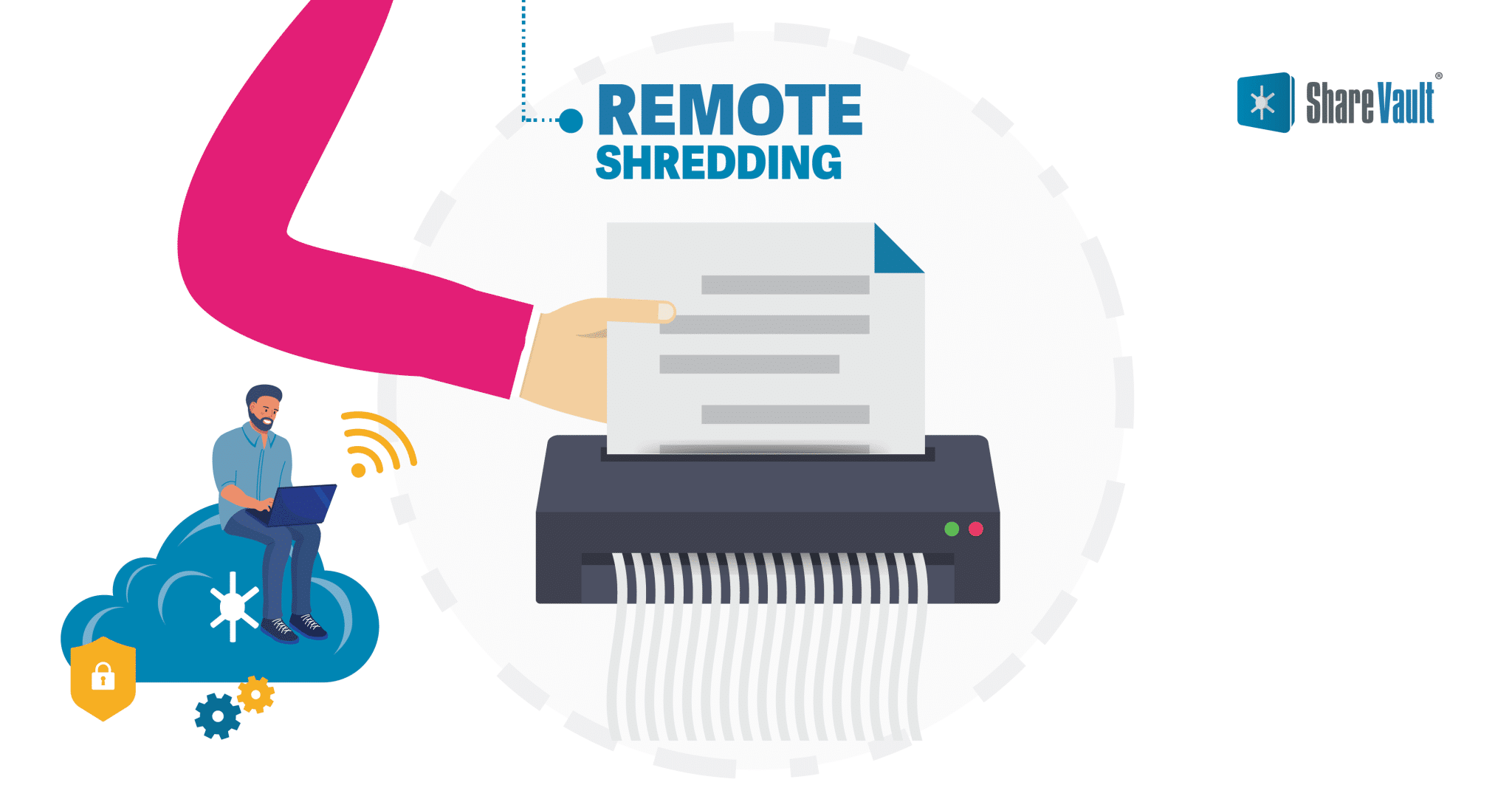
Remote Shredding:
Many virtual data room providers include powerful Information Rights Management (IRM) technology, allowing administrators to retain persistent control over documents shared with third parties. Protected documents are AES-256 bit encrypted and can only be opened by users with current rights, so documents can be remotely “shredded”. In other words, a user’s permission to open a document can be revoked retroactively, even for files already downloaded.
Secure Printing:
Some VDRs include a Secure Print feature which allows users to print to physical printers while preventing printing to PDF. This provides an additional security countermeasure since printing to PDF is the equivalent of being able to save a high fidelity digital copy of the document.
Screen Capture Prevention:
Modern virtual data room features may include the ability to block the screen capture of displayed documents on Windows, Mac, iOS devices and Android devices. Screen Capture Blocking is extremely robust and blocks not only third party screen capture software (such as SnagIt), but also screen recording and screen sharing software (such as GotoMeeting), so your confidential content is displayed only to the intended users.
Configurable Expiration:
VDR policies can be configured by administrators to expire file permissions either on an absolute date or after a relative delay (number of days) from the date / time the files were uploaded. After expiration, the corresponding users will no longer be able to access files to which the policy has been assigned. The optional notification setting, when enabled, sends an email alert to administrators upon expiration.
VDRs with an expiration feature allows administrators to automatically enforce deadlines associated with business workflows. Using this feature in combination with Information Rights Management (IRM), means that even documents that have already been downloaded cannot be opened after expiration.
Fully Configurable Document Policies:
Configurable file security policies, allow administrators to granularly define the appropriate levels of protection for each document. For each policy, admins can specify whether or not users have the right to print, save, copy/paste text, capture the screen, and which, if any, watermark should be applied. These customized policies can then be applied as appropriate to individual documents.
Encryption and Data Privacy
Modern VDRs prioritize data encryption to ensure that information remains secure both in transit and at rest. This means that any data transferred to or stored within the VDR is encrypted using robust encryption protocols, rendering it unreadable to unauthorized parties. Encryption guarantees that even if a breach were to occur, the stolen data would remain inaccessible without the encryption keys.
AES (Advanced Encryption Standard) is today’s encryption standard. It is unparalleled in the amount of security and protection it offers. This advanced encryption standard is used by the National Security Agency (NSA) along with multiple industries, including online banking.
Furthermore, data privacy regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have made encryption a necessity for handling personal and sensitive information. VDRs comply with these regulations by employing encryption standards and implementing features that grant control over data access and sharing permissions, ensuring that only authorized individuals can view, edit, or download sensitive documents.
Multi-Factor Authentication (MFA)
One of the most effective ways to prevent unauthorized access is through the implementation of multi-factor authentication (MFA). This security feature requires users to provide two or more forms of verification before they can access the virtual data room. This could include something they know (password), something they have (a mobile device or security token), or something they are (biometric authentication like fingerprints or facial recognition). MFA significantly reduces the risk of unauthorized access, even if someone manages to obtain a user’s password.
Granular Access Control
Modern VDRs allow administrators to define and control user permissions with granularity. This means that different users or groups can be granted specific levels of access to documents and folders. For instance, an administrator can specify that a user can only view documents but not download or edit them. This level of control ensures that information is shared on a need-to-know basis, minimizing the risk of accidental or intentional data leaks.
Activity Tracking and Auditing
Maintaining an audit trail of user activities within the VDR is crucial for security and accountability. Today’s VDRs track and log every action taken by users, including who accessed a file, when it was accessed, and any modifications made. This activity tracking provides a detailed record that can be crucial for investigating any security breaches or compliance violations.
Watermarking
Virtual data rooms offer features like customized dynamic watermarking, which overlays documents with unique identifiers to trace their origin and distribution. Watermarks are clearly visible, applied diagonally across the page or screen, yet do not interfere with the readability of the underlying text. The watermark text is customizable, and you can embed the following dynamic information:
- User’s email address
- User’s IP address
- Current date
- Current time
Watermarking provides a clear indication to the reader that the content is confidential, and since the user’s identity can be included in the watermark, it allows for a simple but effective deterrent against distribution of the printed documents (if you allow for printing) to unauthorized readers.
Secure Document Viewing
To prevent unauthorized downloads and distribution of sensitive documents, many modern VDRs provide secure document viewing. This feature allows users to view documents within the VDR without the ability to download or save them locally. This way, even if a user’s device is compromised, the documents remain within the controlled environment of the VDR.
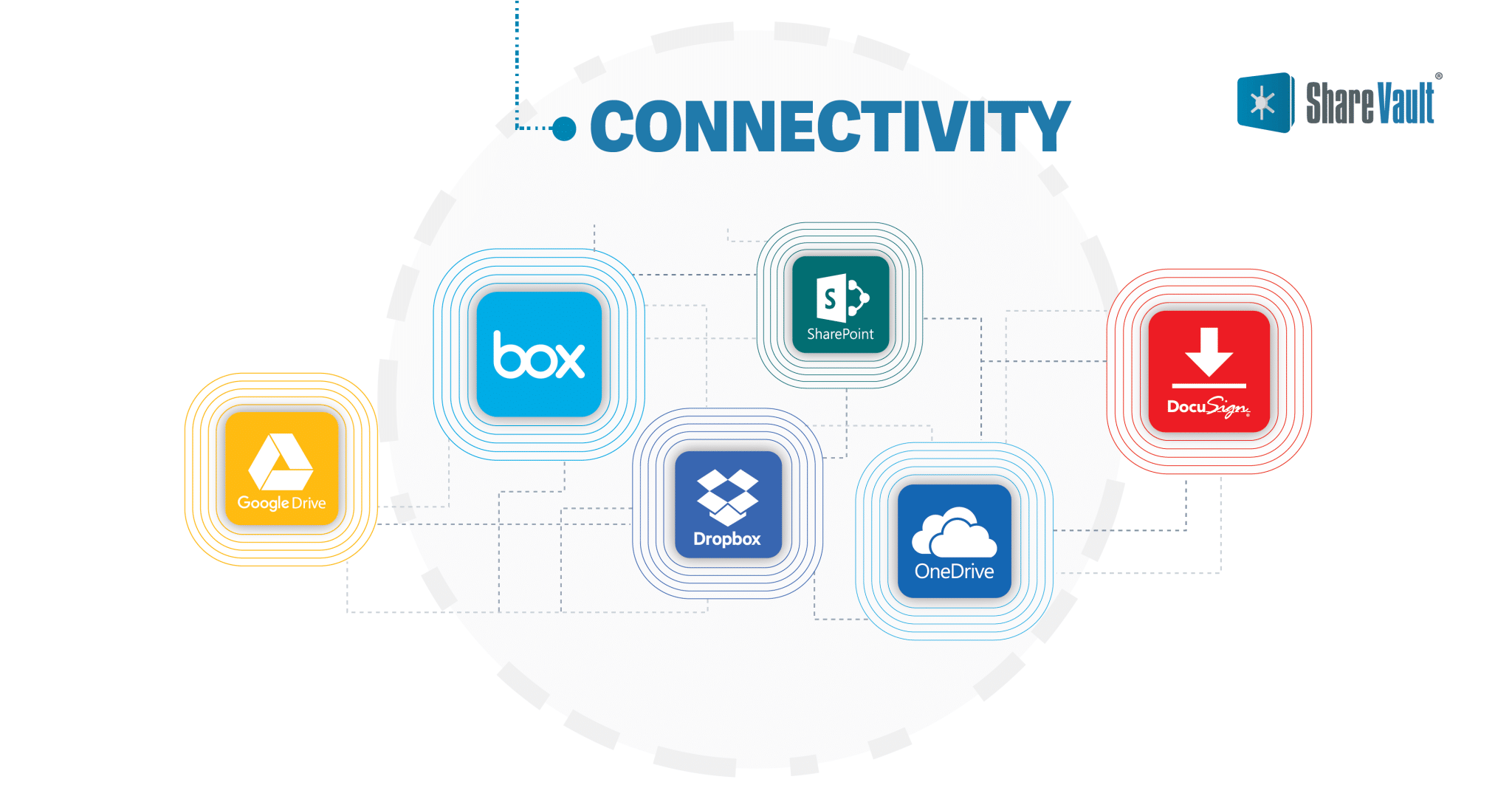
Connectivity
Some VDR providers feature easy-to-configure connectors for Box, Dropbox, Google Drive, Microsoft SharePoint and OneDrive. These connectors include a powerful sync engine, so content is automatically kept up-to-date whenever the source files or folders are added, modified, renamed or deleted.
Some VDRs even have connectors to eSignature platforms like Docusign, so you can add eSignature workflows from right within the secure environment of the VDR.
Compliance, Security and Availability
Virtual Data Rooms are frequently used for applications that demand adherence to stringent security standards for protection of sensitive information and industry regulations. Virtual Data rooms offer bank-grade security, privacy, high availability, and compliance with a variety of standards.
Contract Collaboration Platforms
One of the most common document security vulnerabilities is when work-in-progress documents are actively being collaborated on. In response to this vulnerability, some VDR providers have incorporated document collaboration modules within the protected environment of the VDR.
The collaborative review and finalization of a critical document—like an employee agreement or third-party vendor contract—is known as “redlining.” These collaborative platforms enable contributors to make edits much as they would in MS Word or other word processing apps, but their comments are visible in real time, allowing contributors to track and respond to changes more quickly—a feature that significantly improves both speed and accuracy.
As the redlining process proceeds, a detailed audit trail of all comments and changes is maintained, ensuring that no feedback is ever lost, even after changes have been accepted. This is especially important for finance, life sciences, law and other industries in which documents must adhere to a high level of accountability and compliance. These platforms also provide additional security features to protect sensitive information and ensure that only authorized parties have access to the document.
- Role-based Permissions: Users can be assigned specific privileges, such as the right to edit, approve changes, or lock a paragraph, while others can be restricted to only making comments
- Restricted Sections: Individual sections of a document can be restricted from any edits, locking-in the content in those areas to focus edits elsewhere
- Tracking and Versioning: Along with change tracking, these collaboration platforms automatically save every version of a document, which can then be exported with or without the tracked changes
- Data Room Integration: Because these collaboration platforms are built within the secure environment of a virtual data room, documents within the data room can be directly exported to the collaboration platform allowing for a seamless, integrated workflow
Bottom line: the enhanced document security and collaboration features of today’s modern virtual data rooms will continue to play a vital role in protecting sensitive information from unauthorized access, data breaches, and leaks. Encryption, multi-factor authentication, granular access control, activity tracking, watermarking, and secure document viewing collectively contribute to a robust security posture for businesses and organizations.
As the digital landscape continues to evolve, virtual data rooms will likely adapt and integrate even more advanced security measures to stay ahead of emerging threats and provide a safe haven for sensitive data.